SSO in Magnolia PaaS
The instructions on this page focus primarily on the Keycloak side of things to ensure a successful implementation of SSO in PaaS.
| For more information on installing and configuring the SSO Module and securing Magnolia Admincentral Access, check out the SSO module documentation. |
Overview
The Magnolia SSO (single sign-on) module delegates authentication from a Magnolia instance to an OpenID Connect identity and access management application. The current iteration of the module has been successfully tested with open source Keycloak and cloud identity management software Okta, but all providers that follow the protocol should also be supported.
As Magnolia is already capable of full-fledged security, the intent is to only replace the authentication mechanism. A user on a third-party system with roles and groups is mapped to the equivalent Magnolia user roles and groups.
Keycloak settings for SSO
To integrate an external IDP / Directory Service for Single-Sign-On (SSO) with PaaS, it’s possible to setup a connection via SAML or OpenID Connect (OIDC).
- Example: Azure AD Integration with Keycloak via OpenID Connect (OIDC)
-
As OIDC is the preferred way, the following instructions explain the basic Integration steps for Keycloak and Azure AD via OIDC authentication (OAuth2 for authorization). To integrate an existing Azure AD with Keycloak via OIDC, the following steps are required to be performed (ordered). All
AzureActions are performed via Microsoft Azure portal.
An Azure AD Premium P1/P2 subscription is required to map AppRoles to Users/Groups in Azure later.
|
Basic setup
-
Create
Enterprise Applicationand ShareApplicationID(ie.1978A428-FY151-4EDA-AA40-FB18DCB7F482)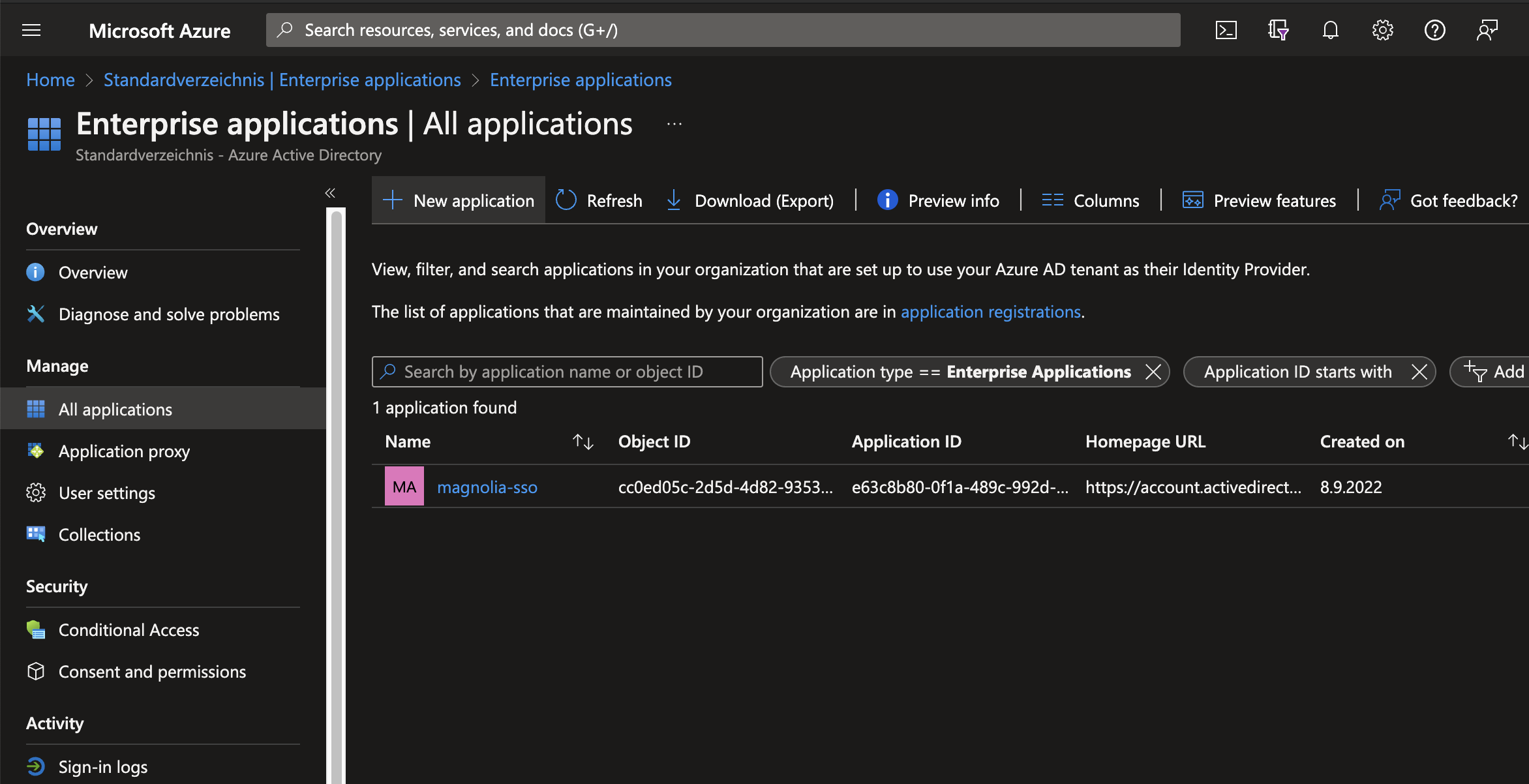
-
Create
Secret→ Securely(!) and share the newSecret Value.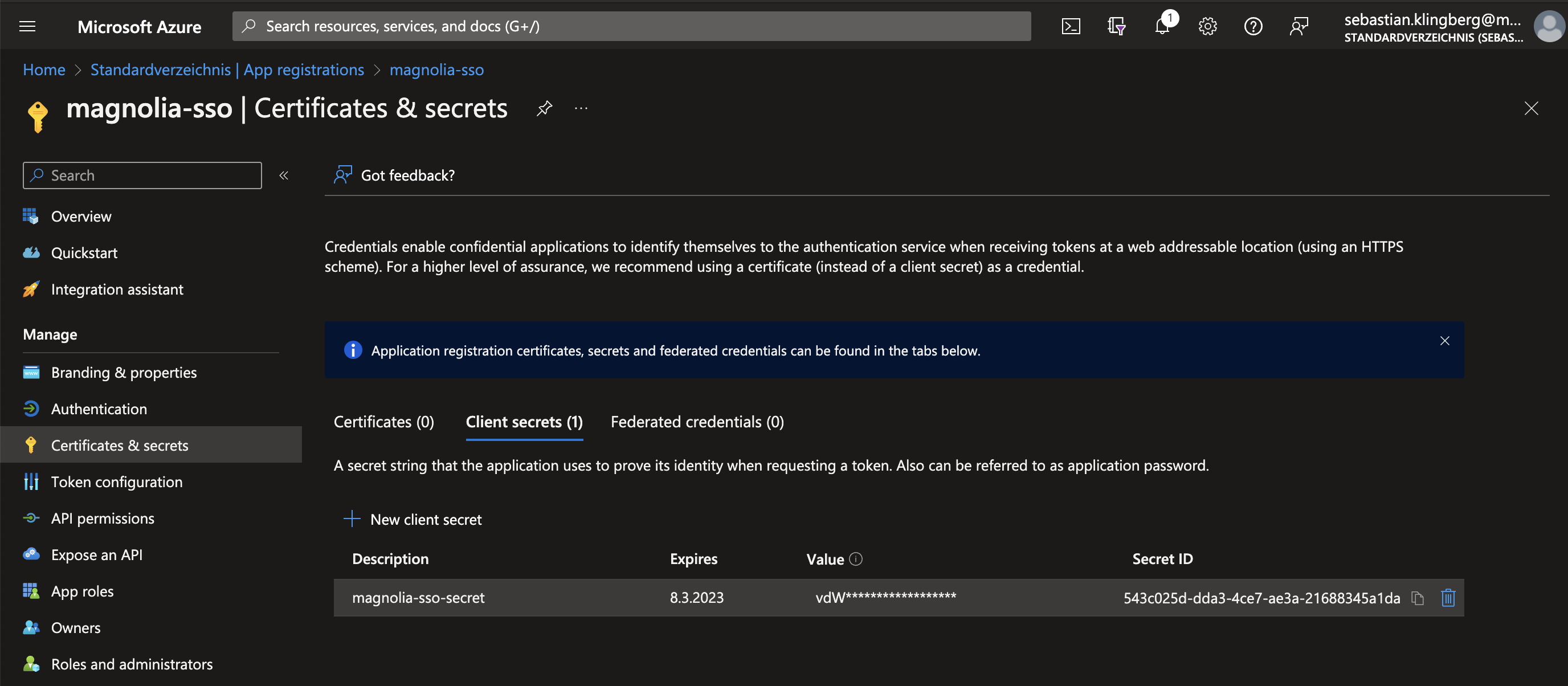
-
In
Overview > Endpoints, copy and share the OpenID Metadata Document URL of the new Application to be entered in Keycloak.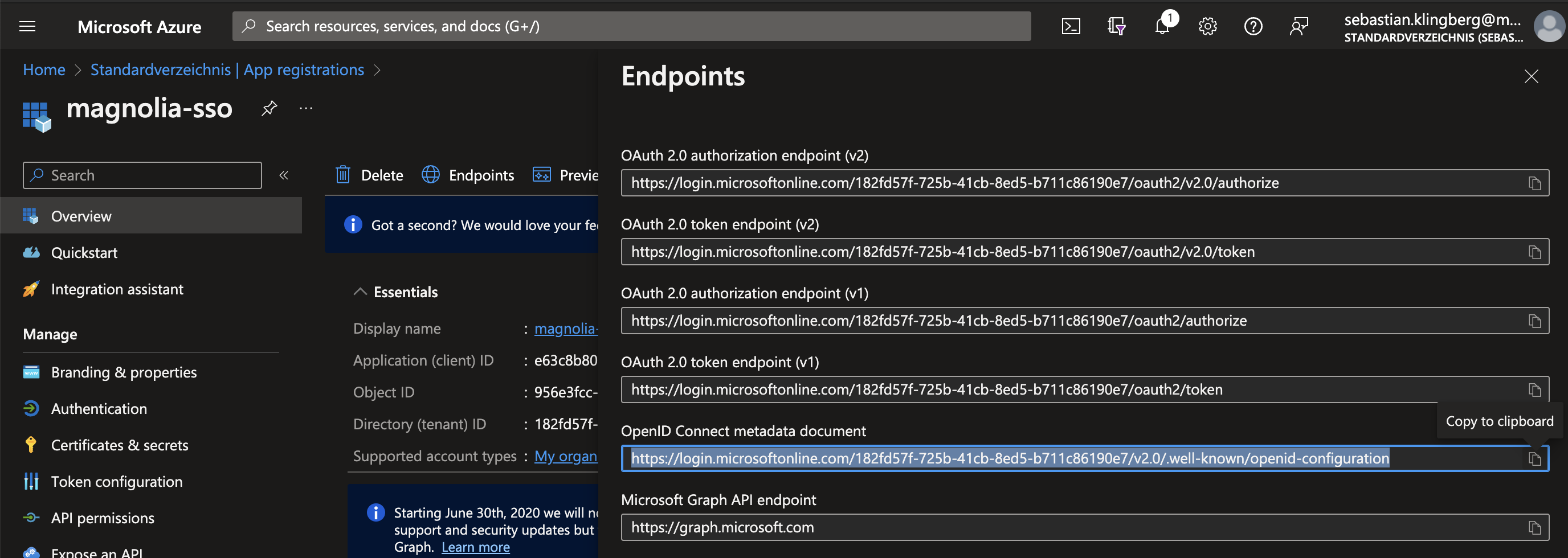
.well-knownmetadocument Formathttps://login.microsoftonline.com/<app-uuid>/v2.0/.well-known/openid-configuration.
-
In
<customer> > Identity Providers, create a new IDP using the information from above:Fetch OIDC Metadata Document to "autofill" basic Information
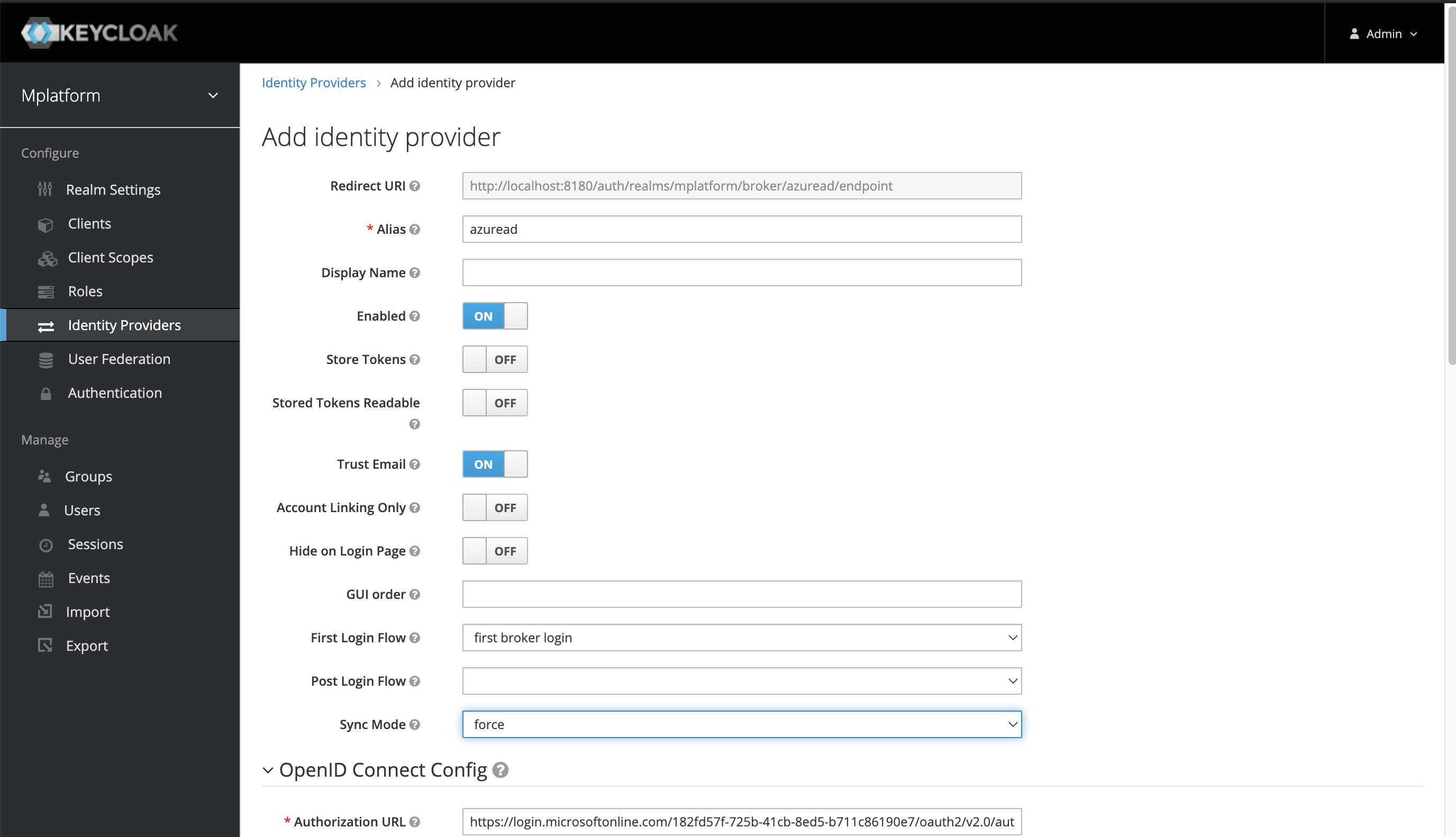
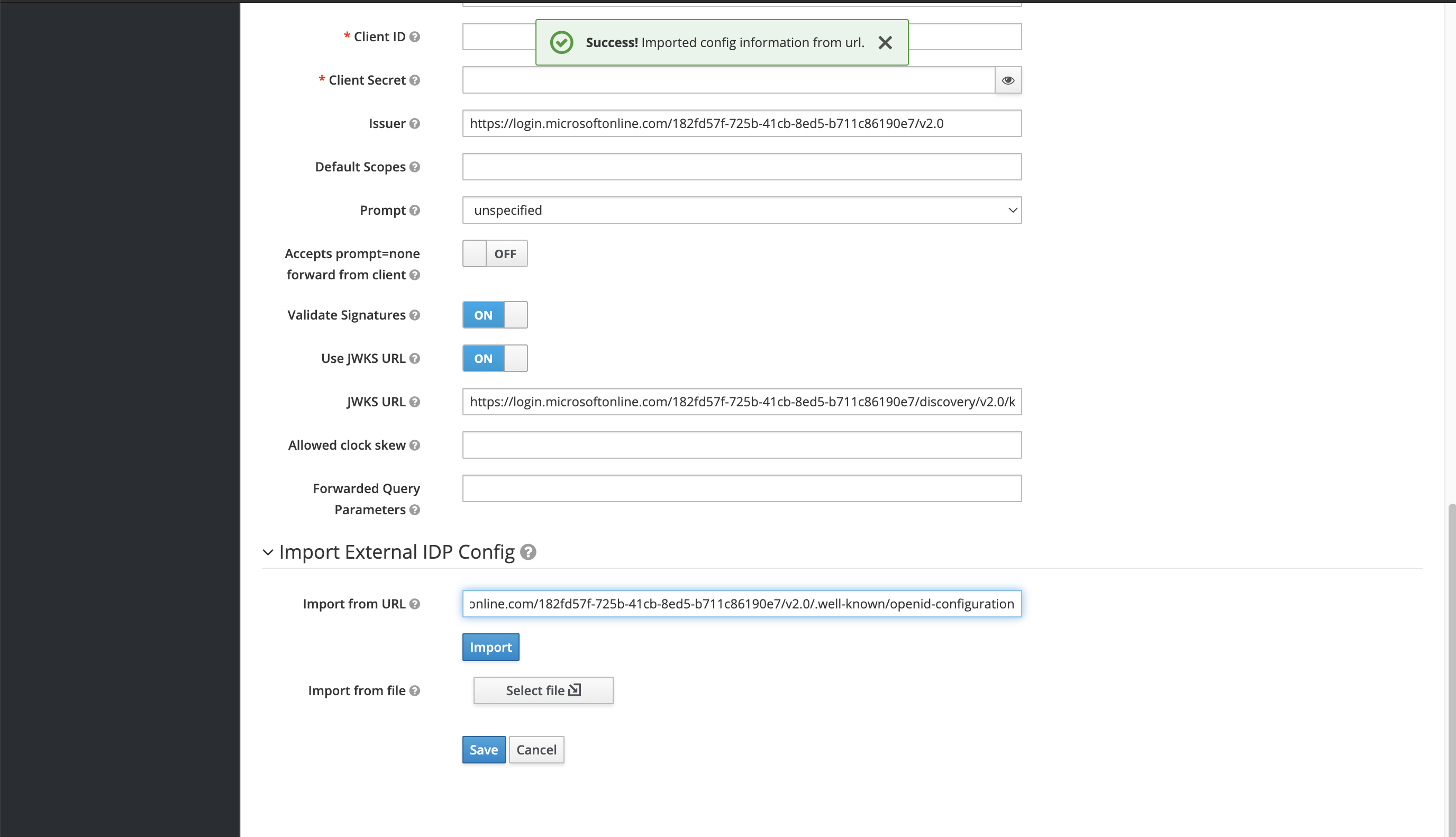
-
ClientID → Enter Azure App
ApplicationID -
ClientSecret → Enter Azure App
Secret Value.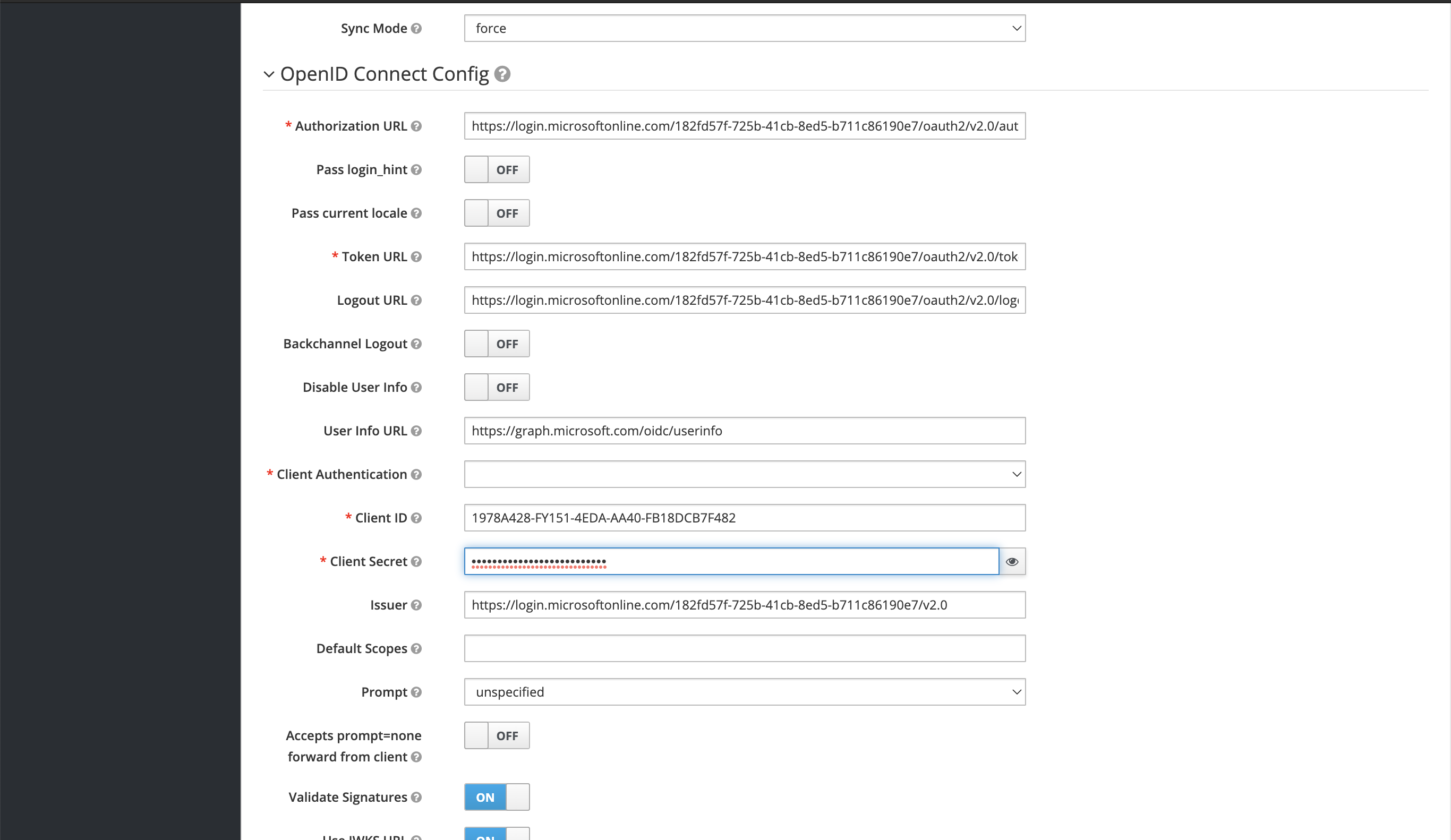
-
Perform a basic Test on Realm ID.
See the URL format https://id.magnolia-platform.com/auth/realms/<customer>/account/#/. -
Prepare
RoleMapping(Map OpenID "roles" to exisiting keycloak roles).
App mapping
-
Ensure Enterprise Application has the RedirectURI set → (format link:https://id.magnolia-platform.com/auth/realms/<customer>/broker/oidc/endpoint).
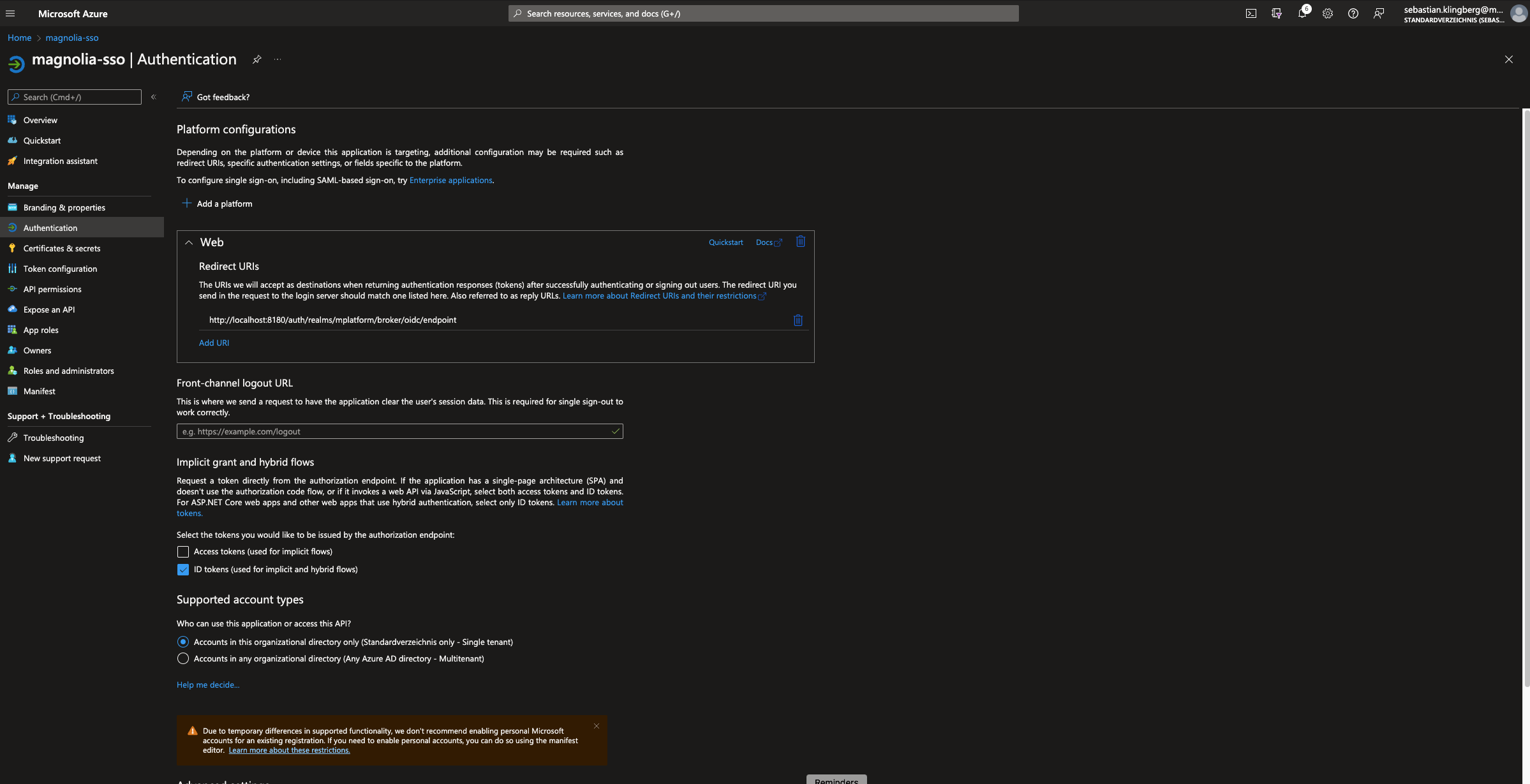
Create multiple RedirectURIs, ie. for production usage AND local testing. -
Now create your desired
AppRole(ie. Magnolia, Cockpit, Rancher). -
In
AppRole, set up OIDC Token Claim to be matched by Keycloak (Value=Claim Valuein Keycloak).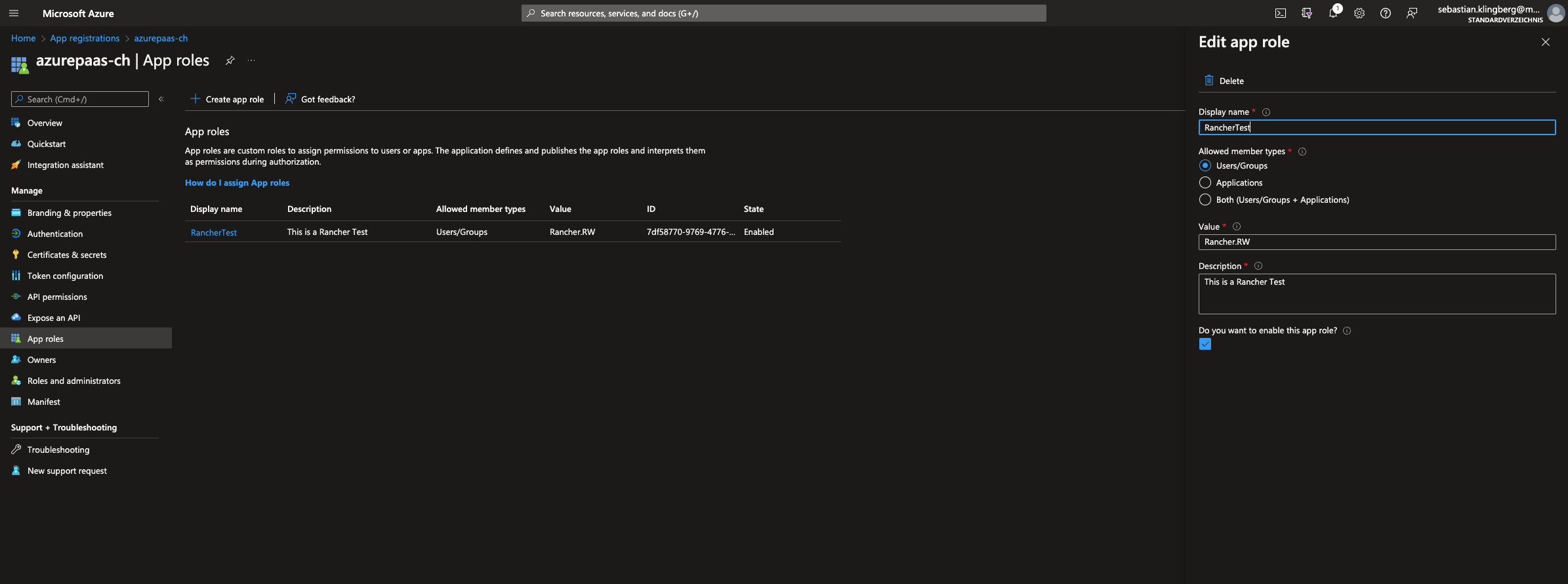
-
Map the
AppRoleto existing Users/Groups in AzureAD.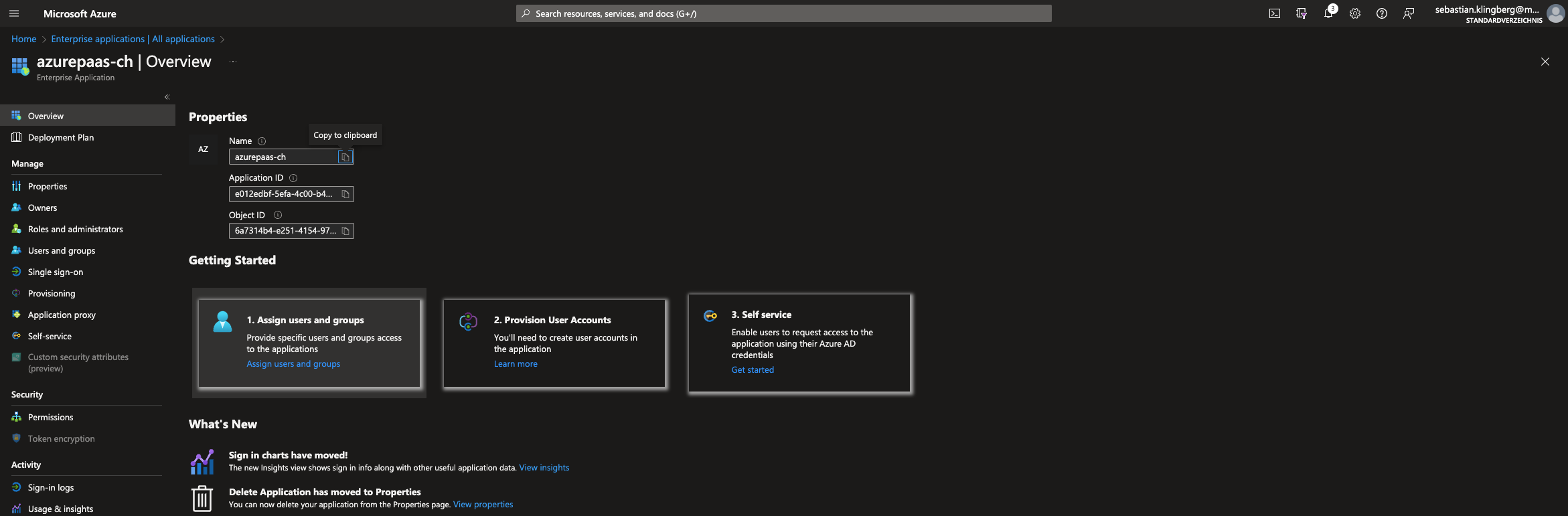
-
Verify the User/Group has the
AppRoleand they can useAppRegistration.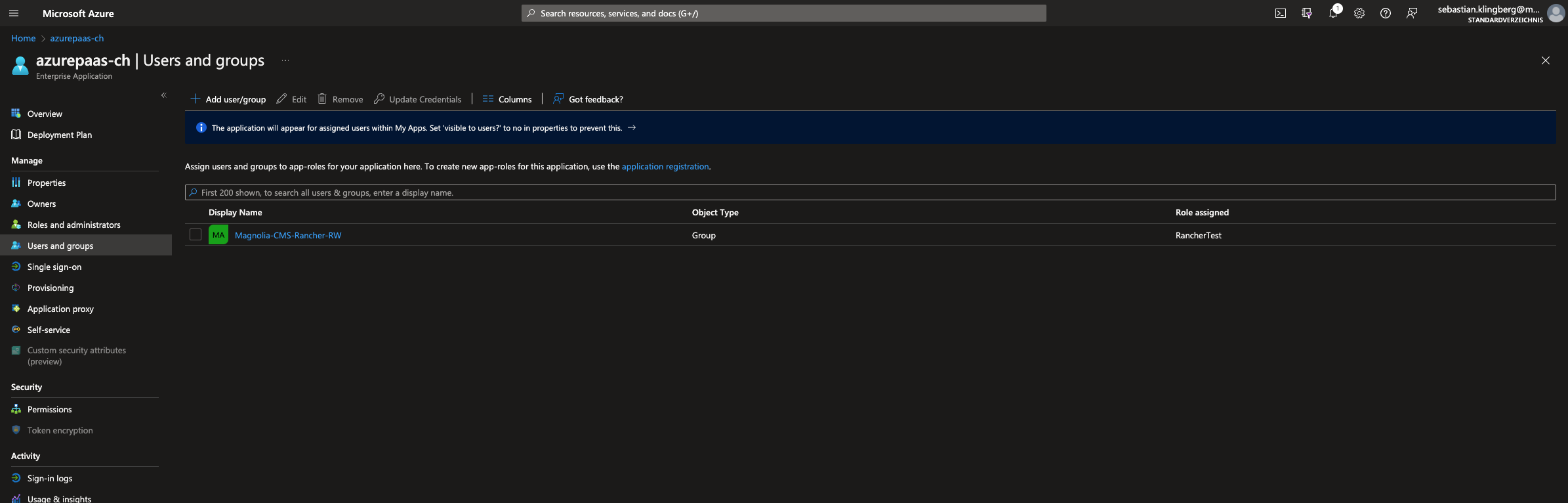
In <customer> > Identity Providers > Mappers map Claim Value (set prior in Azure AppRole) of OIDC Token Claim roles to existing Role in Keycloak IDP
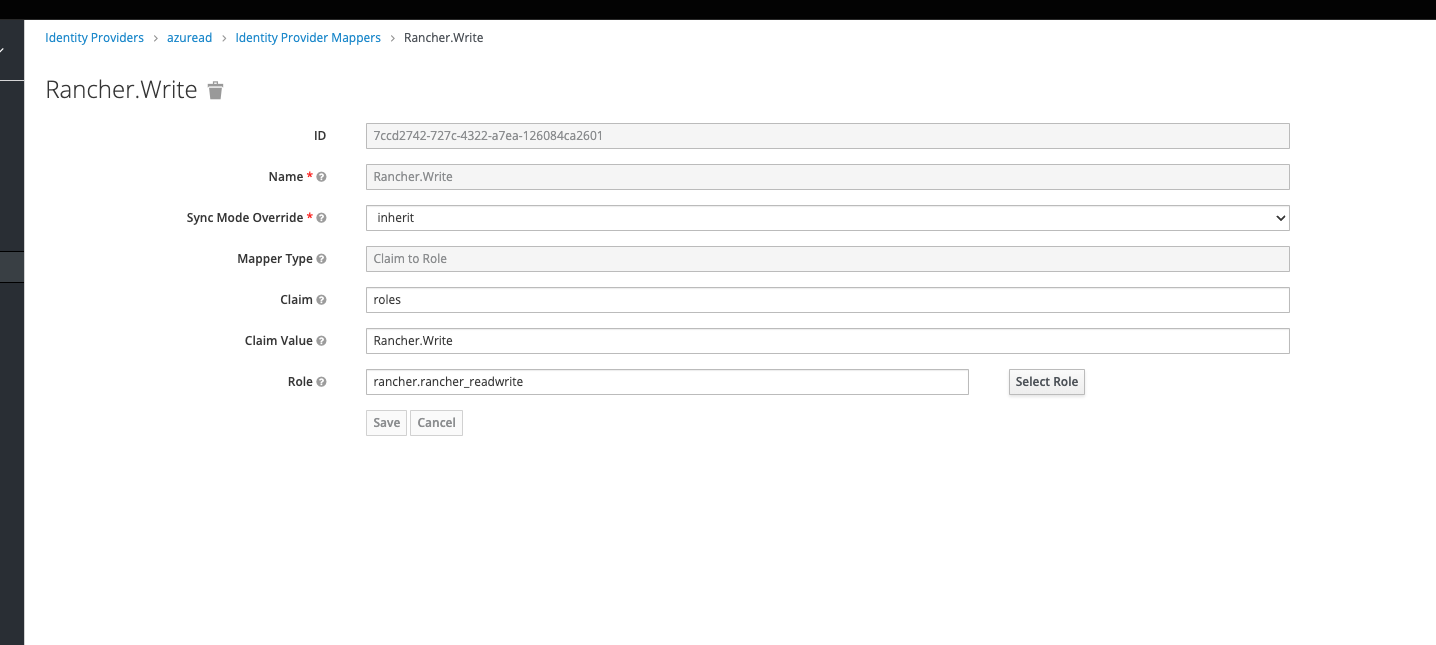
As Naming and the IDP structure of group/user/role assignments could be handled very free and open, it’s important for SSO to align and match on certain role assignments additions to control granular access privileges.
The following default values can be used to prepare an IDP for onboarding with Magnolia Keycloak:
| Claim-Value/Role | Type | Description |
|---|---|---|
|
Rancher |
Rancher Admin Access (all Clusters) |
|
PaaS Cockpit |
Cockpit Admin Access (all functions) |
|
Magnolia Admincentral SSO |
Magnolia Author Superuser Access |
|
Magnolia Publisher SSO |
Magnolia Author Publisher Access |
|
Repeat the steps of App mapping per Application you want to integrate. For more information on installing and configuring the SSO Module and securing Magnolia Admincentral Access, check out the SSO module documentation. |