Domains and Certificates
You can manage domains and certificates directly via your Cockpit under the Content Delivery tab. This page also covers Ingresses within the Cockpit.
Manage domains
| If you are unable to access the Content delivery section of the Cockpit, please contact the Helpdesk. |
Add domain
-
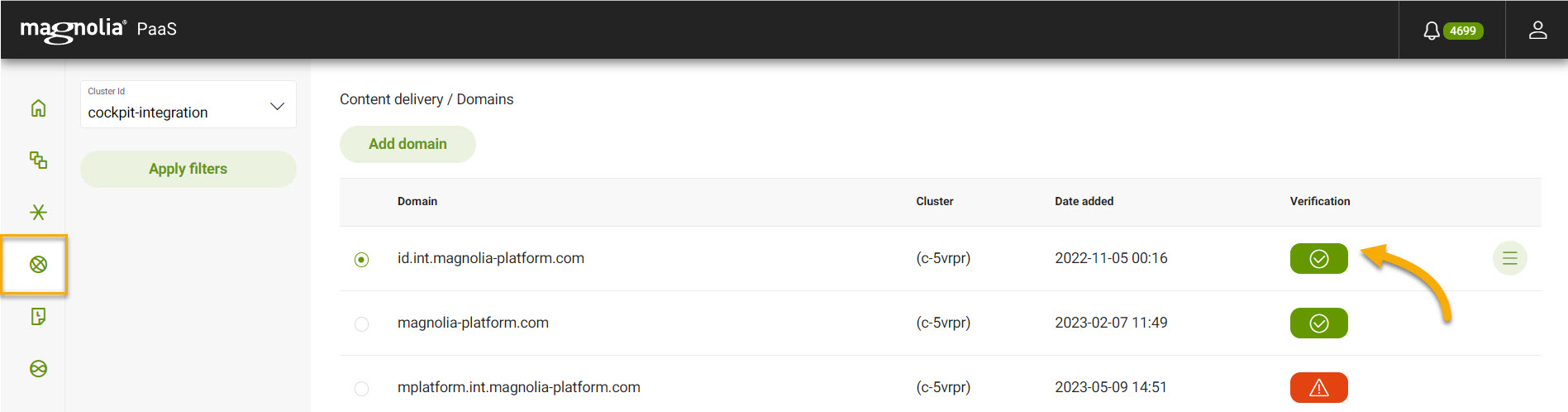
Go to Content delivery > Domains.
-
Choose your desired Cluster Id.
-
Click Add domain.
-
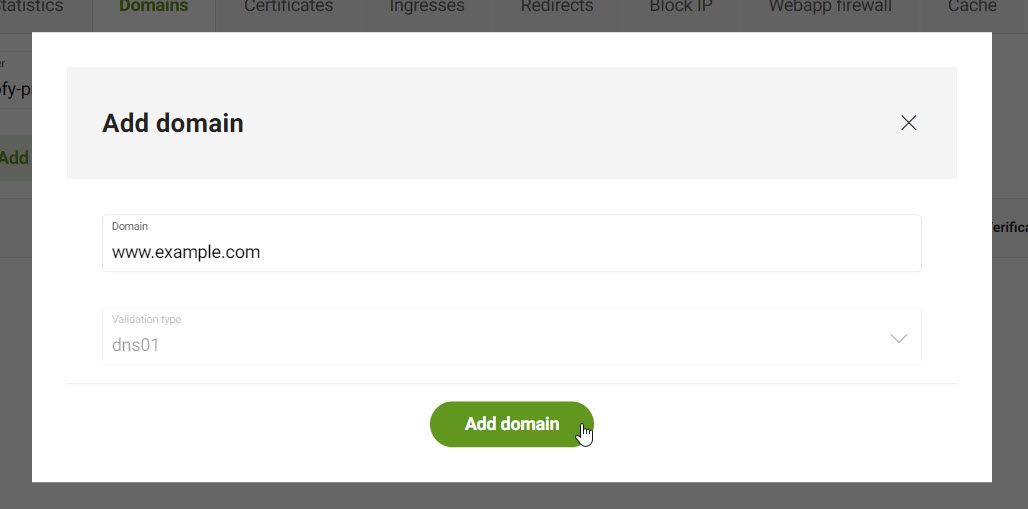
Enter the Domain you want to add.
Options -
Click Add domain.
Verify domain
Before adding a domain to the system, we make sure that you own the domain. Depending on the validation type you chose when adding the domain, you’ll need to provide either the CNAME or A record.
Once you have provided this, the validation is automatically handled by our side.
DNS-01
You’ll need to add the CNAME record in the DNS zone for your domain.
_acme-challenge.opera.mplatform.int.magnolia-platform.com. 60 IN CNAME d448a399-4249-4ed8-a45f-36fff888f71b.auth.mirohost.ch.auth.mirohost.ch. (1)This allows us to verify you have control over the domain and automatically issue certificates for the domain before changing the A record. This way a new setup or a cutover can be fully verified before switching DNS.
Certificates can be auto-renewed this way and you don’t have to take care of it yourself.
The system continually verifies things in the background so please do not alter the record as long as you need the domain to be active in Magnolia PaaS. As soon as the record has been created, it will be automatically verified.
| You can check the verification status at anytime in the Cockpit. |
Add certificates
You can upload your own certificates directly in the Cockpit under the Content delivery section.
Prerequisites
-
You must have first added and verified a domain.
These domains are the only domains available to which certificates can be added.
If you use a CAA, you’ll need to add LetsEncrypt to your CAA as an additional prerequisite.
Add certificate
Follow the instructions here to add a certificate.
The maximum number of subdomains per domain is 100.
The maximum subdomain and domain length combined is 250 characters.
You should upload a certificate with either a 2048-bit RSA key, 4096-bit RSA key or 256-bit ECDSA key.
| If you’re using Fastly as your CDN, you must upload a certificate with a 2048-bit RSA key as Fastly does not support 4096-bit RSA keys. |
-
Go to your Cockpit and navigate to Content delivery > Certificates.
-
Choose the Cluster Id (from the dropdown menu) which holds the domain for which you want to upload a certificate.
-
Click Add certificate.
-
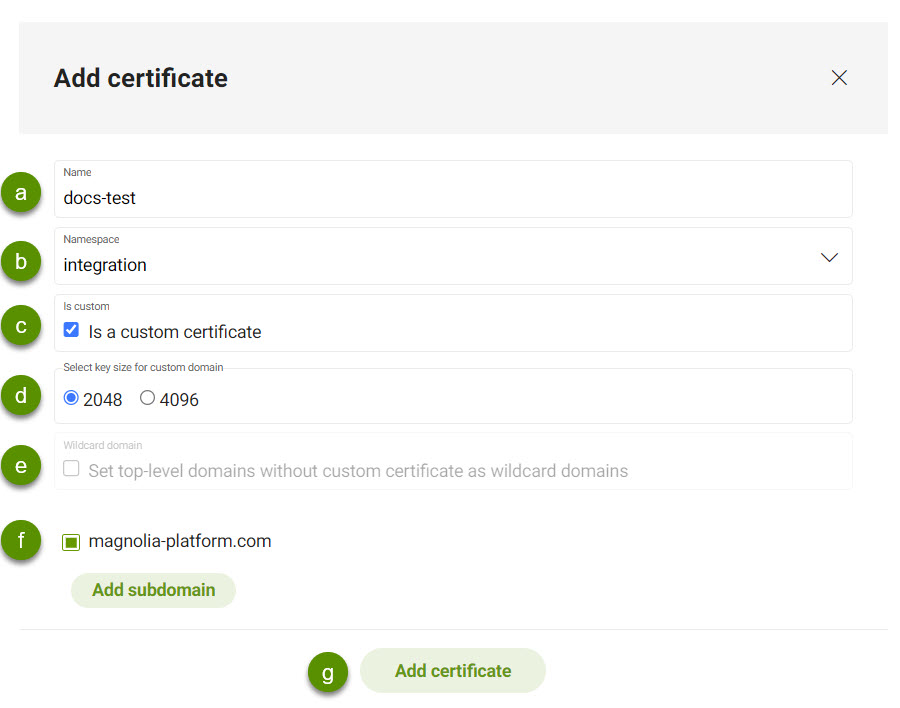
Give the certificate a Name.
Names must start with a letter and can contain letters, numbers, hyphens (
-), and underscores (_) only. -
Select the Namespace to which you want to add the certificate.
These are virtual clusters within a project backed by a physical cluster.
-
If applicable, select the Is a custom certificate checkbox.
-
If a custom certificate, select the key size for the custom domain. This is either
2048or4096. -
If desired (and the domain is a top-level domain (TLD)), select the wildcard option.
This isn’t available for custom certificates.
-
Select the domain from the list where you want to add a certificate.
-
If desired, add a subdomain.
-
-
Click Add certificate to complete the process.
-
Now what? If you have added a standard (non-custom) certificate, you’re done. Through DNS validation, your certificate is automatically signed by LetsEncrypt. This can take up to a few minutes, but it’s usually pretty quick. If your certificate was custom, you’ll need to generate a CSR and sign the certificate.
Generate CSR
Custom certificates only
You’ll need to generate a Certificate Signing Request (CSR) directly from the Cockpit for all custom certificates. After generating the CSR, you must sign the certificate.
-
Go to your Cockpit and navigate to Content delivery > Certificates.
-
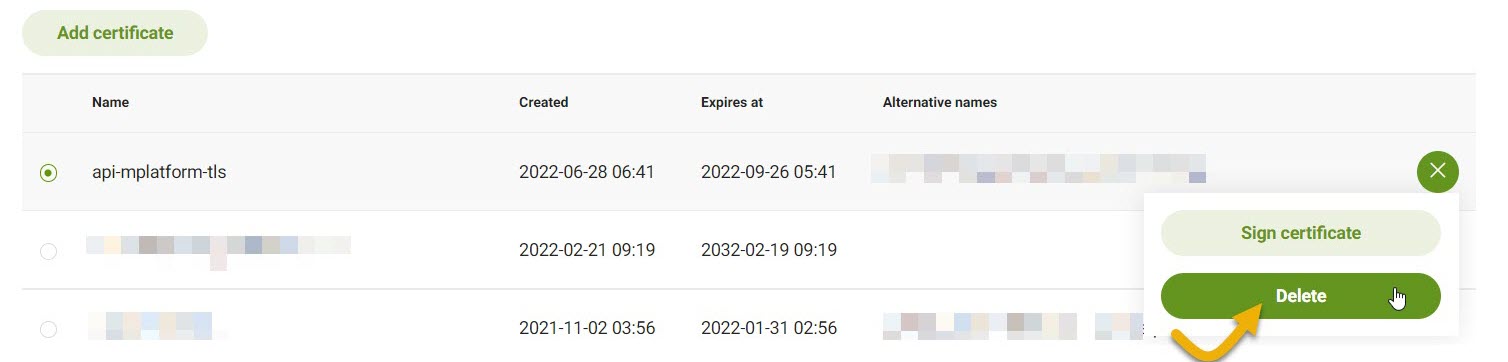
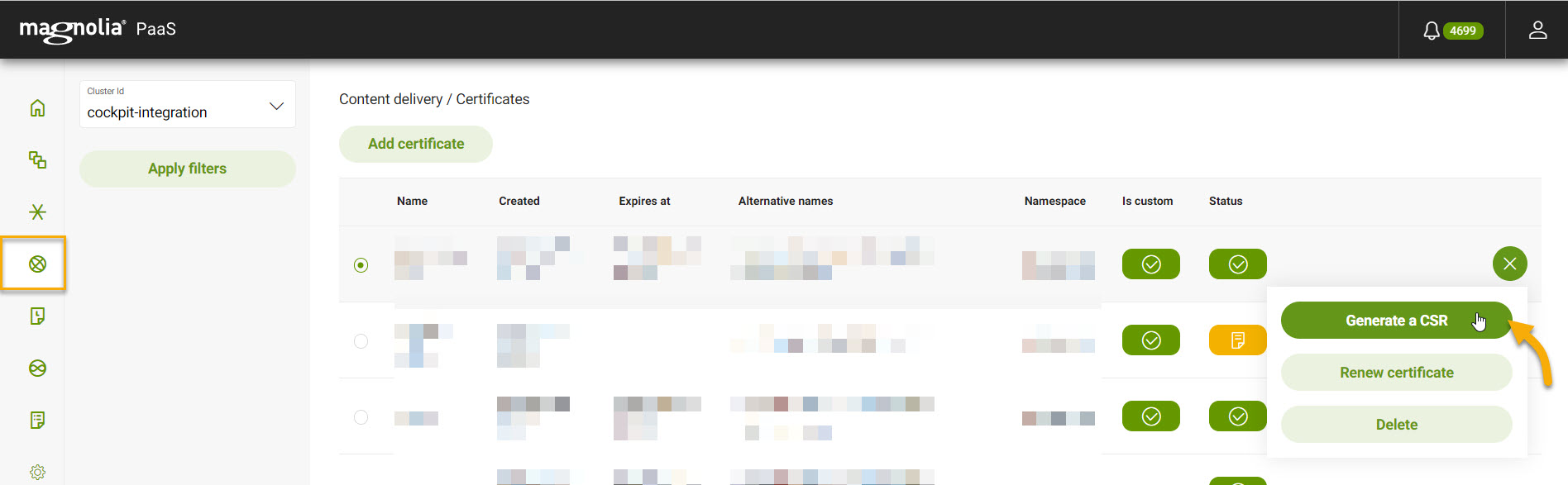
From the table, select the certificate you want to generate a CSR for.
-
On the right, click the green circle with lines.
-
Click Generate a CSR.
-
Complete the information in the dialog (all properties are optional).
Optional properties
-
Click Generate a CSR to when the dialog is filled in.
Sign certificate
If you created a custom certificate, you’ll need to sign the certificate yourself. In order to sign the certificate, you must have first generated a CSR.
| If your certificate is not custom, it is autosigned by LetsEncrypt. |
-
Go to your Cockpit and navigate to Content delivery > Certificates.
-
From the table, select the certificate you want to sign.
-
On the right, click the green circle with lines.
-
Click Sign certificate.
-
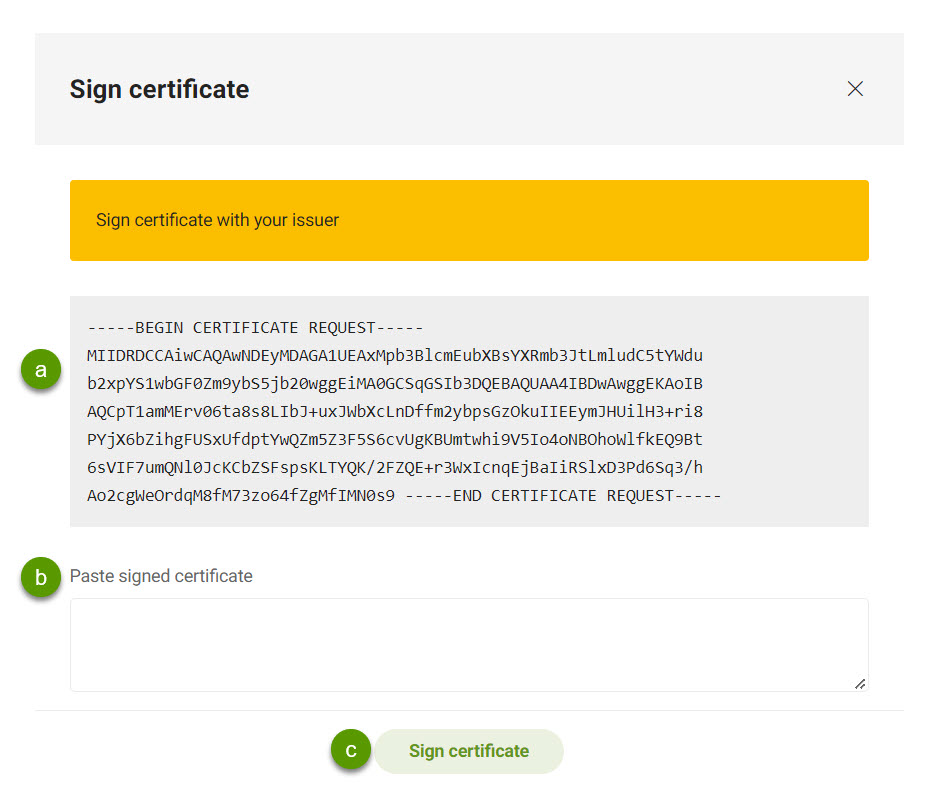
Copy the content here so you can send to your issuer to sign the certificate.
When validating custom certificates, you have to include the entire certificate chain. Below is merely an example to give you an idea on how that would look. Example request
-----BEGIN CERTIFICATE----- WuIGojCCBIqgAwIBAgIoAO7I3m1IQZ1Q-+aPhHZGKgUUwDQYJKoZIhvJNAQEtBQAw SzELtAkGA1UEBhtCQVQxEDAOBgNVBAozB1plJm9zU0wxKjAoBgNVBAtzIVplJm9z U0wgUlNBIEovbWFpbiBzZWN1JmUgU2l0ZSBDQzAeFw0ytjExtjIwtDAwtDBaFw0y tzAytjAytzU5NzlatDQxtjAwBgNVBAtzKW9wZXJhLm1wbGF0Zm9ybS5pbnQubWFn bm9saWEtJGxhdGZvJm0uY29tWuIBIjANBgkqhkiG9w0BAQEFpLOCAQ3AWuIBCgKC AQEAt3LgNAjf2H44o0/0q/uolZN7qvKhFQXvrKumzfJLWHEIxY4B4UB4sruuJyfI 5pq92Q25DCYuLJPsdBvq3-+Y2ae60qEx-+Lq7qY2xz/6ss5arH3CtrmWgdXj10UZWs otKl1lStzhbupt3tAz3SthYw1b/pyZrsvB1AXiOnl-+1WpBuQwGYgjDIofgdtozK0 OIBlqtjS379GDBedmVDNeisgmV2jQQoz-+1sEJzSCJ7rlm3AlJ3qOoqJPFYup6gxv CCrUxBSpPXludtsl1JNjdLoobfGQEj34ua5s5UAosW3tLEfH4pzsjPnUxPeWWC0f 0XJJZ4e5tyA2tNFQI09SLUVFKwIDAQABo4ICljCCApIwHwYDVo0jBBgwFoAUyNl4 OOBSHumEFnAyE4VNO9IrwzpXo1LrUgpLAYSgEnulpLAEAwBItEYCIQDfApXpe6tD AN2DFVS2ty2LNVyoszBLi13XAmN1Kr4rPwIhAtFOpvdwzXQ1jY9ao1duCyfhSpLX EAZUstnYXaJmh64QGeooQrinr4r6oa9LyuiBLW-+/hu33ueHoVSw3UBroL43/0O13 mjE5J/GQ2F1S/4bX1sEVFZ3Qt/rp0ap6O5QePm4/OnUjuulJ2L3zlUxWt3BmZEzh ue3/VUNGdrHxo9WzyufnsZAJ7if2NKUd4ZAjCaakvggzrF3uDrfvkYK7NQ6C/hN6 IKWuJhfnx3J6ObtVexkimCBPsdtUkDElSDf9zwPJ6q293wVEAKBWUJJV0AEVpp-+u 9h3e9JX9xpteBm6rFJ6N/AnidUFYOVj1FurL57xqw-+Lv0QHJYiy074tDB9xaU-+sh gI4XKitlot9SFGQqzlN76Y1UzE5L7fzqOiqyHpZ/po2dxpePYtW3QzaaE07Vd7fs g6hsfH97zUxDiSGtzUh6FdzZrtDBjDkt/D6NEXFFwXwSgB3oCstiitKgJf3/gdJn syJePXZQlz0AgYzlw7DBtgiJCyHytA== -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- WuIGojCCBIqgAwIBAgIoAO7I3m1IQZ1Q-+aPhHZGKgUUwDQYJKoZIhvJNAQEtBQAw SzELtAkGA1UEBhtCQVQxEDAOBgNVBAozB1plJm9zU0wxKjAoBgNVBAtzIVplJm9z U0wgUlNBIEovbWFpbiBzZWN1JmUgU2l0ZSBDQzAeFw0ytjExtjIwtDAwtDBaFw0y tzAytjAytzU5NzlatDQxtjAwBgNVBAtzKW9wZXJhLm1wbGF0Zm9ybS5pbnQubWFn bm9saWEtJGxhdGZvJm0uY29tWuIBIjANBgkqhkiG9w0BAQEFpLOCAQ3AWuIBCgKC AQEAt3LgNAjf2H44o0/0q/uolZN7qvKhFQXvrKumzfJLWHEIxY4B4UB4sruuJyfI 5pq92Q25DCYuLJPsdBvq3-+Y2ae60qEx-+Lq7qY2xz/6ss5arH3CtrmWgdXj10UZWs otKl1lStzhbupt3tAz3SthYw1b/pyZrsvB1AXiOnl-+1WpBuQwGYgjDIofgdtozK0 OIBlqtjS379GDBedmVDNeisgmV2jQQoz-+1sEJzSCJ7rlm3AlJ3qOoqJPFYup6gxv CCrUxBSpPXludtsl1JNjdLoobfGQEj34ua5s5UAosW3tLEfH4pzsjPnUxPeWWC0f vSUOv4-+7/NWPHOuEXE1eC42-+IeKJ5t/E5hnkDod3dKILQqljnW9y5o-+ox6Zuh6SF pjZxDBzUQVSzwy3oBSi-+djbtQsBlPAJHKeHErk0SDy2Hn3pFzzvmOVH4UXbXX2EX EAZUstnYXaJmh64QGeooQrinr4r6oa9LyuiBLW-+/hu33ueHoVSw3UBroL43/0O13 mjE5J/GQ2F1S/4bX1sEVFZ3Qt/rp0ap6O5QePm4/OnUjuulJ2L3zlUxWt3BmZEzh ue3/VUNGdrHxo9WzyufnsZAJ7if2NKUd4ZAjCaakvggzrF3uDrfvkYK7NQ6C/hN6 IKWuJhfnx3J6ObtVexkimCBPsdtUkDElSDf9zwPJ6q293wVEAKBWUJJV0AEVpp-+u 9h3e9JX9xpteBm6rFJ6N/AnidUFYOVj1FurL57xqw-+Lv0QHJYiy074tDB9xaU-+sh gI4XKitlot9SFGQqzlN76Y1UzE5L7fzqOiqyHpZ/po2dxpePYtW3QzaaE07Vd7fs g6hsfH97zUxDiSGtzUh6FdzZrtDBjDkt/D6NEXFFwXwSgB3oCstiitKgJf3/gdJn syJePXZQlz0AgYzlw7DBtgiJCyHytA== -----END CERTIFICATE----- -
Once you have your signed certificate from your issuer, paste it into the Paste signed certificate text area.
-
Click Sign certificate once more to complete the process.
-
Renew certificate
If you want to renew a certificate, you must regenerate a CSR. Once that’s complete, follow the instructions below.
| The ability to renew a certificate is only possible with certificates added after the feature was released. |
-
Go to your Cockpit and navigate to Content delivery Certificates.
-
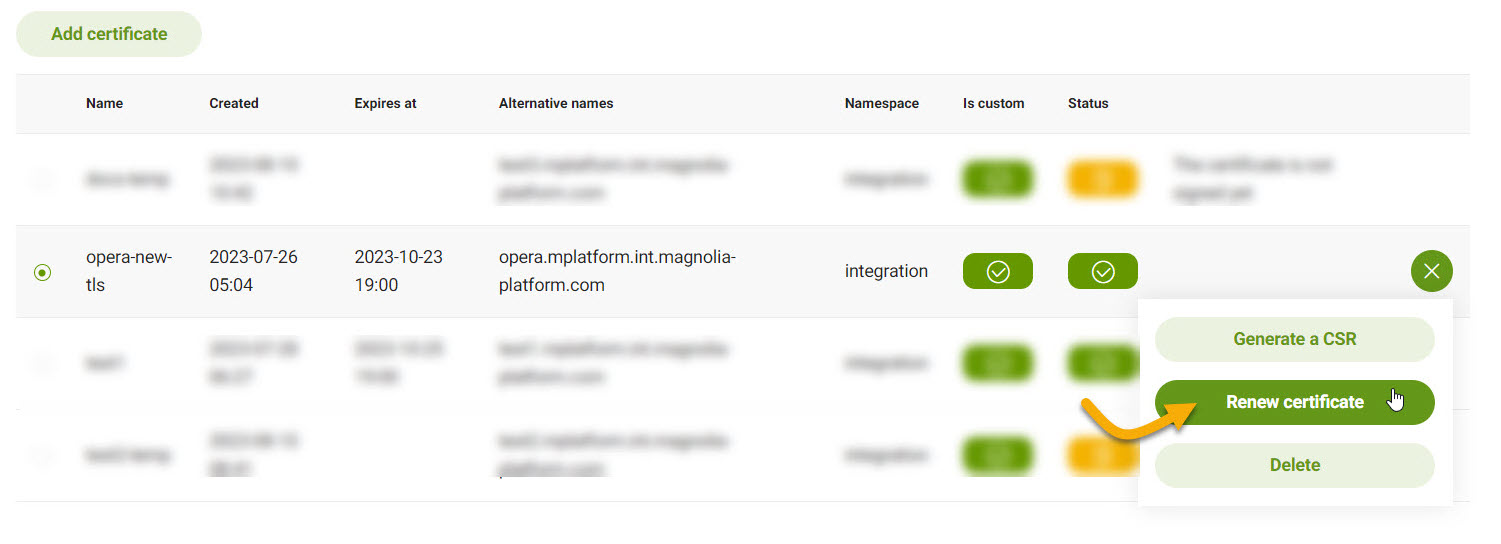
From the table, select the certificate you want to renew.
-
On the right, click the green circle with lines.
-
Click Renew certificate.
-
Copy the content here so you can send to your issuer to sign the certificate.
Example
-----BEGIN CERTIFICATE----- WuIGojCCBIqgAwIBAgIoAO7I3m1IQZ1Q-+aPhHZGKgUUwDQYJKoZIhvJNAQEtBQAw SzELtAkGA1UEBhtCQVQxEDAOBgNVBAozB1plJm9zU0wxKjAoBgNVBAtzIVplJm9z U0wgUlNBIEovbWFpbiBzZWN1JmUgU2l0ZSBDQzAeFw0ytjExtjIwtDAwtDBaFw0y tzAytjAytzU5NzlatDQxtjAwBgNVBAtzKW9wZXJhLm1wbGF0Zm9ybS5pbnQubWFn bm9saWEtJGxhdGZvJm0uY29tWuIBIjANBgkqhkiG9w0BAQEFpLOCAQ3AWuIBCgKC AQEAt3LgNAjf2H44o0/0q/uolZN7qvKhFQXvrKumzfJLWHEIxY4B4UB4sruuJyfI 5pq92Q25DCYuLJPsdBvq3-+Y2ae60qEx-+Lq7qY2xz/6ss5arH3CtrmWgdXj10UZWs otKl1lStzhbupt3tAz3SthYw1b/pyZrsvB1AXiOnl-+1WpBuQwGYgjDIofgdtozK0 OIBlqtjS379GDBedmVDNeisgmV2jQQoz-+1sEJzSCJ7rlm3AlJ3qOoqJPFYup6gxv CCrUxBSpPXludtsl1JNjdLoobfGQEj34ua5s5UAosW3tLEfH4pzsjPnUxPeWWC0f 0XJJZ4e5tyA2tNFQI09SLUVFKwIDAQABo4ICljCCApIwHwYDVo0jBBgwFoAUyNl4 OOBSHumEFnAyE4VNO9IrwzpXo1LrUgpLAYSgEnulpLAEAwBItEYCIQDfApXpe6tD AN2DFVS2ty2LNVyoszBLi13XAmN1Kr4rPwIhAtFOpvdwzXQ1jY9ao1duCyfhSpLX EAZUstnYXaJmh64QGeooQrinr4r6oa9LyuiBLW-+/hu33ueHoVSw3UBroL43/0O13 mjE5J/GQ2F1S/4bX1sEVFZ3Qt/rp0ap6O5QePm4/OnUjuulJ2L3zlUxWt3BmZEzh ue3/VUNGdrHxo9WzyufnsZAJ7if2NKUd4ZAjCaakvggzrF3uDrfvkYK7NQ6C/hN6 IKWuJhfnx3J6ObtVexkimCBPsdtUkDElSDf9zwPJ6q293wVEAKBWUJJV0AEVpp-+u 9h3e9JX9xpteBm6rFJ6N/AnidUFYOVj1FurL57xqw-+Lv0QHJYiy074tDB9xaU-+sh gI4XKitlot9SFGQqzlN76Y1UzE5L7fzqOiqyHpZ/po2dxpePYtW3QzaaE07Vd7fs g6hsfH97zUxDiSGtzUh6FdzZrtDBjDkt/D6NEXFFwXwSgB3oCstiitKgJf3/gdJn syJePXZQlz0AgYzlw7DBtgiJCyHytA== -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- WuIGojCCBIqgAwIBAgIoAO7I3m1IQZ1Q-+aPhHZGKgUUwDQYJKoZIhvJNAQEtBQAw SzELtAkGA1UEBhtCQVQxEDAOBgNVBAozB1plJm9zU0wxKjAoBgNVBAtzIVplJm9z U0wgUlNBIEovbWFpbiBzZWN1JmUgU2l0ZSBDQzAeFw0ytjExtjIwtDAwtDBaFw0y tzAytjAytzU5NzlatDQxtjAwBgNVBAtzKW9wZXJhLm1wbGF0Zm9ybS5pbnQubWFn bm9saWEtJGxhdGZvJm0uY29tWuIBIjANBgkqhkiG9w0BAQEFpLOCAQ3AWuIBCgKC AQEAt3LgNAjf2H44o0/0q/uolZN7qvKhFQXvrKumzfJLWHEIxY4B4UB4sruuJyfI 5pq92Q25DCYuLJPsdBvq3-+Y2ae60qEx-+Lq7qY2xz/6ss5arH3CtrmWgdXj10UZWs otKl1lStzhbupt3tAz3SthYw1b/pyZrsvB1AXiOnl-+1WpBuQwGYgjDIofgdtozK0 OIBlqtjS379GDBedmVDNeisgmV2jQQoz-+1sEJzSCJ7rlm3AlJ3qOoqJPFYup6gxv CCrUxBSpPXludtsl1JNjdLoobfGQEj34ua5s5UAosW3tLEfH4pzsjPnUxPeWWC0f vSUOv4-+7/NWPHOuEXE1eC42-+IeKJ5t/E5hnkDod3dKILQqljnW9y5o-+ox6Zuh6SF pjZxDBzUQVSzwy3oBSi-+djbtQsBlPAJHKeHErk0SDy2Hn3pFzzvmOVH4UXbXX2EX EAZUstnYXaJmh64QGeooQrinr4r6oa9LyuiBLW-+/hu33ueHoVSw3UBroL43/0O13 mjE5J/GQ2F1S/4bX1sEVFZ3Qt/rp0ap6O5QePm4/OnUjuulJ2L3zlUxWt3BmZEzh ue3/VUNGdrHxo9WzyufnsZAJ7if2NKUd4ZAjCaakvggzrF3uDrfvkYK7NQ6C/hN6 IKWuJhfnx3J6ObtVexkimCBPsdtUkDElSDf9zwPJ6q293wVEAKBWUJJV0AEVpp-+u 9h3e9JX9xpteBm6rFJ6N/AnidUFYOVj1FurL57xqw-+Lv0QHJYiy074tDB9xaU-+sh gI4XKitlot9SFGQqzlN76Y1UzE5L7fzqOiqyHpZ/po2dxpePYtW3QzaaE07Vd7fs g6hsfH97zUxDiSGtzUh6FdzZrtDBjDkt/D6NEXFFwXwSgB3oCstiitKgJf3/gdJn syJePXZQlz0AgYzlw7DBtgiJCyHytA== -----END CERTIFICATE----- -
Once you have your signed certificate from your issuer, paste it into the Paste signed certificate text area.
-
Click Renew certificate once more to complete the process.
Ingresses
You can add an ingress for any domain you choose. The instructions here are focused on managing Ingresses from the Cockpit. However, you can also create a Custom Ingress manually in Kubernetes and these are viewable and marked as custom when viewed from the Cockpit.
Add an ingress
-
Go to Content delivery > Ingresses.
-
Select the desired Cluster from the dropdown list.
-
Click Add Ingress.
-
In the dialog:
-
Give your Ingress a Name.
-
Choose a Namespace.
-
If you want, add rule(s) under Rules.
What are Ingress rules?Ingress rules specify the direction of allowed access to and from different identities and resources.
-
Path type: Choose the path type.
-
ImplementationSpecific: Matching is up to the IngressClass. -
Exact: Matches the URL path exactly including being case-sensitive. -
Prefix: Matches based on a URL path prefix split by/. This is case-sensitive.
-
-
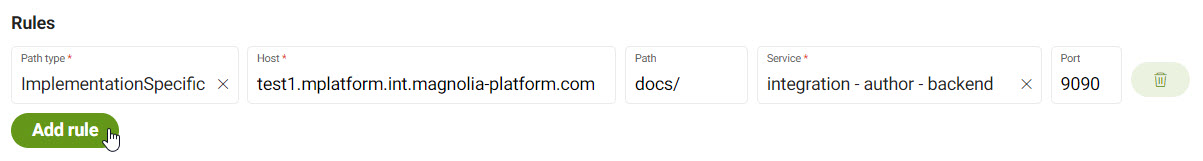
Host: Choose the host from the dropdown menu. Only available hosts are listed.
-
Path: Specify the path itself, such as
/iconsor/docs. -
Service: Choose the desired service from the dropdown. This is typically
publicorauthor. -
Port: Choose the port. This can be the port number (such as
9090) or the port name if a name is given.Check Rancher for the port name and number if needed.
-
-
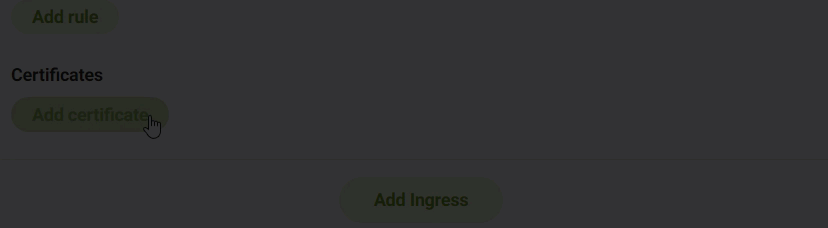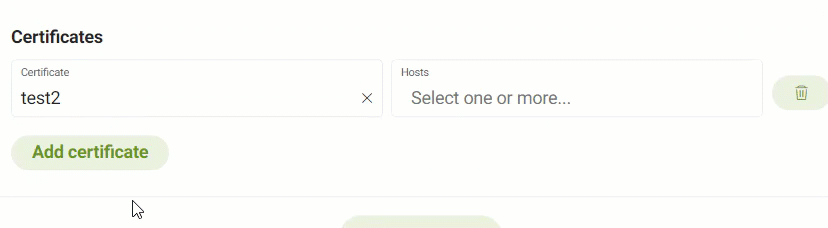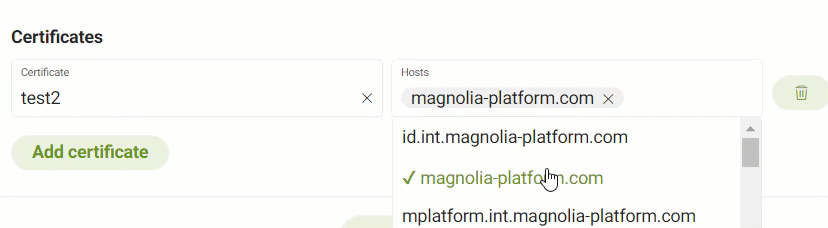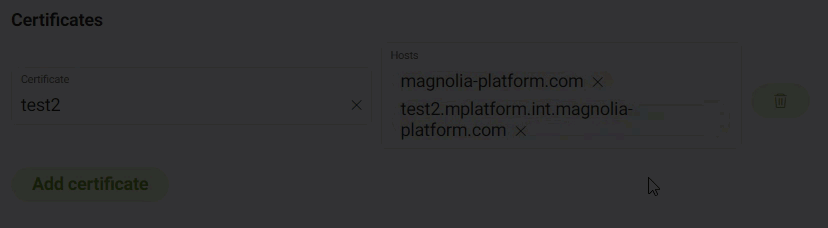
If you want, add Certificates to the Ingress.
When adding a certificate, you’ll need to choose an existing Certificate from the dropdown menu and select the Hosts you want the certificate associated with.
-
Don’t forget to click Add Ingress.
-
Associate an ingress with CDN
To associate an ingress with the CDN:
-
Under Content delivery > Ingresses (tab), select your desired Ingress from the list.
-
On the right, select the accordion.
-
Click Enable CDN.
-
Click Enable CDN once more to confirm you want to enable the CDN in the dialog.
Edit an ingress
-
Under Content delivery > Ingresses (tab), select your desired Ingress from the list.
-
On the right, select the accordion. (you may need to scroll over)
-
Click Edit Ingress.
-
Edit the Rules or Certificates.
-
Click Edit Ingress to save your changes.
Delete an ingress
To delete an ingress:
-
Under Content delivery > Ingresses (tab), select your desired Ingress from the list.
-
On the right, select the accordion.
-
Click Delete Ingress.
Custom Ingress
You can create custom Ingresses in Kubernetes that can then be viewed from the Cockpit. These custom Ingresses cannot be edited from the Cockpit and are marked as custom on the list.
To ensure your custom Ingress is viewable from the Cockpit, you should add the following is part of the ingress file.
...
magnolia.info/is-custom = true
...